Page 350 - The Secret War in the Italian front in WWI (1915-1918)
P. 350
THE SECRET WAR ON THE ITALIAN FRONT IN WWI (1915 – 1918)
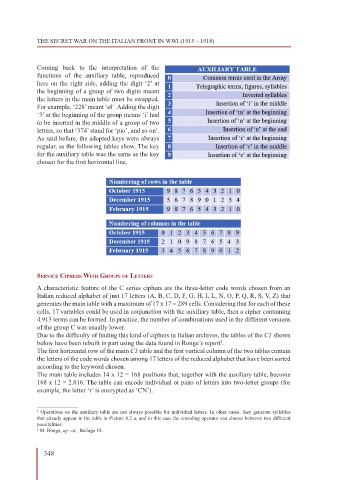
Coming back to the interpretation of the
functions of the auxiliary table, reproduced
here on the right side, adding the digit ‘2’ at
the beginning of a group of two digits meant
the letters in the main table must be swapped.
For example, ‘228’ meant ‘el’. Adding the digit
‘3’ at the beginning of the group means ‘i’ had
to be inserted in the middle of a group of two
letters, so that ‘374’ stand for ‘pio’, and so on .
1
As said before, the adopted keys were always
regular, as the following tables show. The key
for the auxiliary table was the same as the key
chosen for the first horizontal line.
servIce cIPhers wITh grouPs of leTTers
A characteristic feature of the C series ciphers are the three-letter code words chosen from an
Italian reduced alphabet of just 17 letters (A, B, C, D, F, G, H, I, L, N, O, P, Q, R, S, V, Z) that
generates the main table with a maximum of 17 x 17 = 289 cells. Considering that for each of these
cells, 17 variables could be used in conjunction with the auxiliary table, then a cipher containing
4.913 terms can be formed. In practice, the number of combinations used in the different versions
of the group C was usually lower.
Due to the difficulty of finding this kind of ciphers in Italian archives, the tables of the C1 shown
below have been rebuilt in part using the data found in Ronge’s report .
2
The first horizontal row of the main C1 table and the first vertical column of the two tables contain
the letters of the code words chosen among 17 letters of the reduced alphabet that have been sorted
according to the keyword chosen.
The main table includes 14 x 12 = 168 positions that, together with the auxiliary table, become
168 x 12 = 2.016. The table can encode individual or pairs of letters into two-letter groups (for
example, the letter ‘r’ is encrypted as ‘CN’).
1 Operations on the auxiliary table are not always possible for individual letters. In other cases, they generate syllables
that already appear in the table in Picture 8.2 a, and in this case the encoding operator can choose between two different
possibilities.
2 M. Ronge, op. cit., Beilage 18.
348