Page 161 - The Secret War in the Italian front in WWI (1915-1918)
P. 161
CHAPTER EIGHT
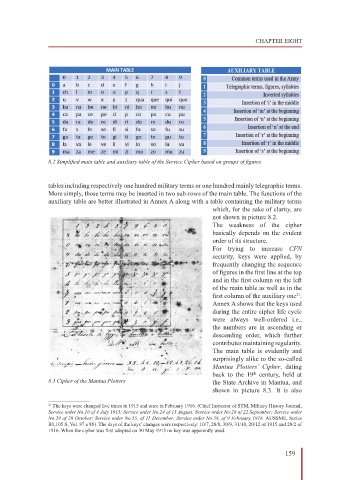
8.2 Simplified main table and auxiliary table of the Service Cipher based on groups of figures
tables including respectively one hundred military terms or one hundred mainly telegraphic terms.
More simply, those terms may be inserted in two sub-rows of the main table. The functions of the
auxiliary table are better illustrated in Annex A along with a table containing the military terms
which, for the sake of clarity, are
not shown in picture 8.2.
The weakness of the cipher
basically depends on the evident
order of its structure.
For trying to increase CFN
security, keys were applied, by
frequently changing the sequence
of figures in the first line at the top
and in the first column on the left
of the main table as well as in the
first column of the auxiliary one .
21
Annex A shows that the keys used
during the entire cipher life cycle
were always well-ordered i.e.,
the numbers are in ascending or
descending order, which further
contributes maintaining regularity.
The main table is evidently and
surprisingly alike to the so-called
Mantua Plotters’ Cipher, dating
back to the 19 century, held at
th
8.3 Cipher of the Mantua Plotters the State Archive in Mantua, and
shown in picture 8.3. It is also
21 The keys were changed five times in 1915 and once in February 1916. (Chief Inspector of STM, Military History Journal,
Service order No.16 of 4 July 1915; Service order No.24 of 13 August; Service order No.28 of 22 September; Service order
No.29 of 20 October; Service order No.35, of 11 December; Service order No.38, of 9 February 1916. AUSSME, Series
B1,105 S, Vol. 87 e 88). The days of the keys’ changes were respectively: 10/7, 20/8, 30/9, 31/10, 20/12 of 1915 and 20/2 of
1916. When the cipher was first adopted on 30 May 1915 no key was apparently used.
159