Page 189 - The Secret War in the Italian front in WWI (1915-1918)
P. 189
CHAPTER NINE
Among the possible countermeasures, the systematic substitution of the Red Code with the Blue
Code “which differs from the Red Code only in the page numbering” was excluded .
19
However, the letter also contains some shoddy suggestions concerning for instance to use the Green
Cover Code for communications between High Commands and the Pocket Military Cipher for other
radio dispatches. The reasons given for these choices were the larger reliability of the former because its
limited usage and the latter pretty secrecy due to variable keys changing every week.
In sum, while the diagnosis seemed correct, the recommended therapy showed evident shortcomings.
Relying on the Pocket Military Cipher was evidently a mistake. On the other hand, the potential
spread of the Green Code - limited in fact during the following months - might have compromised
it, if a further protection by means for instance of an effective second encoding, should had not
been provided.
Contrary to the Intelligence Office suggestion, the Red Code was suspended only temporarily,
probably due to the lack of an effective alternative and it reappeared on 25 April with a different
page numbering and an extremely simple over-coding implemented by adding fixed or periodically
variable numbers to the code groups.
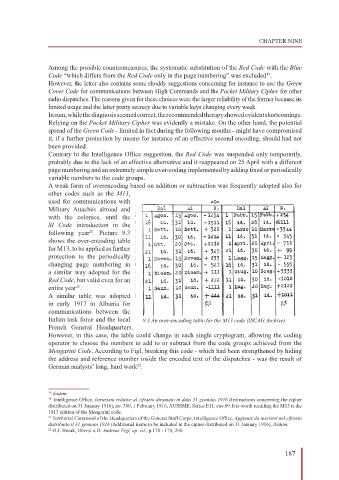
A weak form of overencoding based on addition or subtraction was frequently adopted also for
other codes such as the M13,
used for communications with
Military Attachés abroad and
with the colonies, until the
SI Code introduction in the
following year . Picture 9.3
20
shows the over-encoding table
for M13, to be applied as further
protection to the periodically
changing page numbering in
a similar way adopted for the
Red Code, but valid even for an
entire year .
21
A similar table was adopted
in early 1917 in Albania for
communications between the
Italian task force and the local 9.3 An over-encoding table for the M13 code (ISCAG Archive)
French General Headquarters.
However, in this case, the table could change in each single cryptogram, allowing the coding
operator to choose the numbers to add to or subtract from the code groups achieved from the
Mengarini Code. According to Figl, breaking this code - which had been strengthened by hiding
the address and reference number inside the encoded text of the dispatches - was the result of
German analysts’ long, hard work .
22
19 ibidem.
20 Intelligence Office, Istruzioni relative al cifrario diramato in data 31 gennaio 1916 (Instructions concerning the cipher
distributed on 31 January 1916), no. 380, 1 February 1916, AUSSME, Series E11, env.89.It is worth recalling the M13 is the
1913 edition of the Mengarini code.
21 Territorial Command of the Headquarters of the General Staff Corps, Intelligence Office, Aggiunte da inserirsi nel cifrario
distribuito il 31 gennaio 1916 (Additional items to be included in the cipher distributed on 31 January 1916), ibidem.
22 O.J. Horak, Oberst a.D. Andreas Figl, op. cit., p.178 - 179, 290.
187