Page 125 - The Secret War in the Italian front in WWI (1915-1918)
P. 125
CHAPTER SIX
In substitution methods, the
plaintext elements are replaced by
another conventional sign. The most
famous and ancient among them is
the Caesar cipher, where alphabet
letters are replaced by letters of the
same alphabet shifted by a fixed
interval (A is replaced by C and B
by D, etc.). Those simple mono-
alphabetic ciphers were mostly
substituted, as far back as the 15
th
century, by poly-alphabetic systems
where replacing alphabets are
numerous and chosen, for each letter
or group of letters of the original
message, according to a numerical or
alphabetic key. The first application
of a poly-alphabetical code is Leon
Battista Alberti’s ciphering disc and
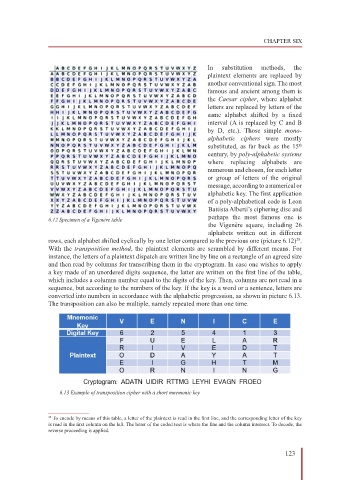
6.12 Specimen of a Vigenère table perhaps the most famous one is
the Vigenère square, including 26
alphabets written out in different
rows, each alphabet shifted cyclically by one letter compared to the previous one (picture 6.12) .
28
With the transposition method, the plaintext elements are scrambled by different means. For
instance, the letters of a plaintext dispatch are written line by line on a rectangle of an agreed size
and then read by columns for transcribing them in the cryptogram. In case one wishes to apply
a key made of an unordered digits sequence, the latter are written on the first line of the table,
which includes a columns number equal to the digits of the key. Then, columns are not read in a
sequence, but according to the numbers of the key. If the key is a word or a sentence, letters are
converted into numbers in accordance with the alphabetic progression, as shown in picture 6.13.
The transposition can also be multiple, namely repeated more than one time.
6.13 Example of transposition cipher with a short mnemonic key
28 To encode by means of this table, a letter of the plaintext is read in the first line, and the corresponding letter of the key
is read in the first column on the left. The letter of the coded text is where the line and the column intersect. To decode, the
reverse proceeding is applied.
123